On the 2nd of August 2022, Solana was trending on Twitter because close to $8 million was stolen from its wallets.
Barely a week before then, the Audius platform was reported to have lost $6 million to a crypto hack.
Sadly, the list does not stop there.

Although cryptocurrencies have grown rapidly and with more sophisticated security systems, hacks have continued to happen.
Keep reading this article to find out why and see how to secure your funds.
Post Summary
- What Is Crypto Hack?
- How Does Crypto Hack Happen?
- List Of Blockchains/Exchanges That Have Been Hacked
- How To Recover From A Crypto Hack
- Conclusion
Click on any item above to read its details immediately.
Let’s get to it!
1. What Is Crypto Hack?

Crypto hack simply means the loss of funds from a crypto wallet or wallets belonging to a blockchain to a thief.
Let’s assume you forgot your wallet somewhere.
Then when you realized it, you went back to get it only to meet it empty.
It means that a thief must have come across it and helped himself, right?
Similarly, when an unauthorized user gains access to a crypto wallet and takes away funds from it, we say that a crypto hack has occurred.
Normally, a crypto hack should not be possible because only the owner of the wallet with its private key should have access to it.
Nevertheless, thieves are everywhere even on the blockchain. Hence, the reason we experience crypto hacks.
Experts like Tom Robinson believe that cryptocurrency companies are “huge honeypots” for hackers.
“Crypto transactions are irreversible, so if a hacker can get their hands on it, it’s very difficult for anyone to retrieve it,” he says.
Also, he added that crypto is attractive because huge paydays are possible without the extra hassle of cybercrime like ransomware, where criminals have to negotiate with hacked companies.
OMG!
But how does a crypto hack happen?
Find out in the next section!
2. How Does Crypto Hack Happen?

A crypto hack can take different forms including:
a. 51% attack
This is when an attacker introduces an altered blockchain because he owns more than 50% of the original blockchain’s computational power.
Thus, he can make changes to transactions that have not been confirmed by the original blockchain.
In other words, he can steal the tokens from transactions that have not been confirmed.
For example, bitcoin transactions are considered successful after six confirmations.
Assuming Ada transferred 1 BTC to a Steven, the transaction would be recorded and confirmed in one block – first confirmation.
Then, that block’s data is recorded into the next block and confirmed – second confirmation.
And so on till the sixth confirmation.
But if a 51% attack happens before then, maybe at the 4th confirmation, that 1 BTC is free for the attacker to steal. Oh My!
[Suggested Read: What Is A 51% Attack? | Coins That Have Suffered It]
b. Mistake in creation
During the creation of a blockchain, errors may occur.
We may call them “automated,” “encrypted,” and the likes but they are still created by man.
And man is prone to make mistakes. Once there is an error in the code used to create a blockchain, it makes it vulnerable to hackers.
Sadly, the hacker may steal as many funds as possible without being detected because of the error in the blockchain.
Frances Coppola (Economist and author) put it this way:
“We’ve seen so many hacks and exploits caused by – to be blunt – frank carelessness and lack of concern for the safety of people’s funds.
Crypto companies are sometimes so anxious to make ‘loadsamoney’, or simply accommodate high demand, that they put out badly designed and tested code, compromise security, or place too much reliance on infrastructure.”
Little wonder you see some crypto platforms offering a bounty for “bug reports” on their websites.
It is a way to encourage users to report any errors they find on the chain before hackers take advantage of it.
People that report bugs found on a protocol are usually rewarded.
c. Bridge hack
Bridges are a recent tech innovation that enables different blockchains to interact with each other.
They are popular in smart contract blockchains like Ethereum, Solana, Polygon, etc.
Unfortunately, they are very vulnerable to hacks because their technology is complex and they are often run by anonymous teams.
So, the way they safeguard funds is often unclear thus making them repeated targets to experienced hackers.
For example, the Horizon bridge of the Harmony blockchain was hacked because the hacker was able to compromise the private information required to access the four wallets managing/securing the bridge.
d. Wallet Hack
Ever heard the saying, “Not your keys, not your coin?”
That is to say, if you’re not the one holding your keys, you can lose your coins to the person holding them for you at any time, which is common with hot wallets.
Hot wallets are the most popular type of wallet, and also the least secure because they are connected to the internet.
Using hot wallets (mobile and web wallets) exposes your funds to hackers.
[Suggested Read: Ultimate Guide: A – Z of Bitcoin Wallets]
Since your private key is saved online, your funds are exposed to hackers.
If a hacker manages to gain access to the server where your keys are saved, he’ll steal your tokens. Sorry!
e. Exchange Hack
When reviewing the quality of a crypto exchange, we often check for security measures.
Terms like cold storage and insurance purse are viewed as green flags.
However, no matter the level of security a crypto exchange offers, it is still weak.
Why?
Generally, exchanges hold cryptocurrency in a reserve wallet for liquidity.
Also, they try to keep customers’ private keys safe in their online servers.
But this is what makes them susceptible to hackers.
Once a thief gains access to the cryptocurrency keys hidden in an exchange, it’s all over.
Let’s now see the exchanges or blockchains that have been hacked before.
Tag along!
3. List Of Blockchains/Exchanges That Have Been Hacked
I searched different crypto news sites and I mentioned all the crypto hacks I found beginning from the most recent.
Check it out:
Crypto Hack List (2022)
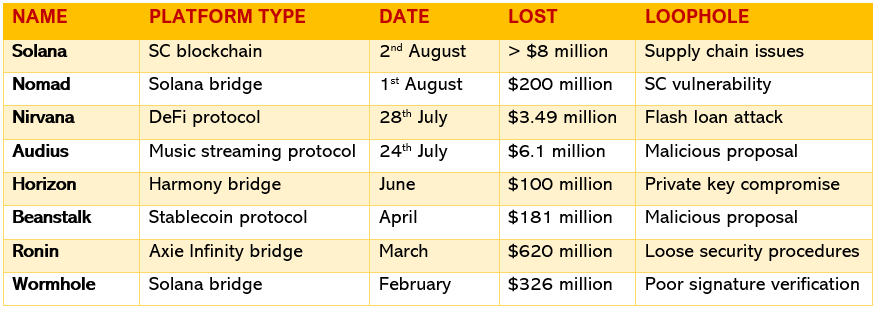
Crypto Hack List (2021)

Crypto Hack List (2020 and earlier)
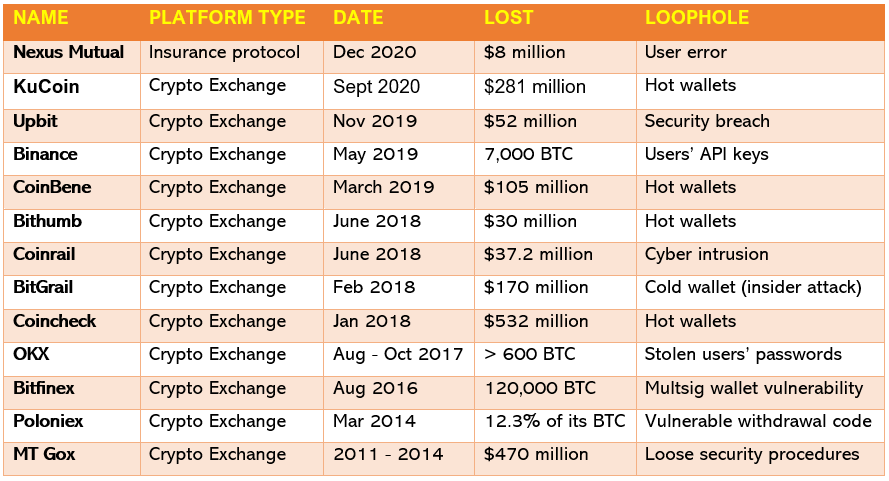
Did you know?
State-sponsored hackers have been identified as the culprits behind some crypto hacks.
In 2021, cryptocurrency researchers at Chainalysis reported that North Korean hackers stole almost $400m worth of digital assets in at least seven attacks on cryptocurrency platforms last year.
https://www.bbc.co.uk/news/business-59990477
Pretty scary, huh?
Let’s see how to recover from a crypto hack in the next section.
Keep reading!
4. How To Recover From A Crypto Hack
Because transactions on the blockchain cannot be reversed, it is very unlikely that funds stolen from a crypto hack will be recovered.
However, it is not impossible. Some hacked exchanges reimburse users’ lost funds, if not all, at least a given percentage.
Also, protocols try to pause all smart contracts within a given time to prevent the hacker from selling off all the stolen coins like in the case of Audius.
Others offer a bounty hoping that the thief will return the funds e.g Nirvana.
Sadly, there are platforms that couldn’t recover from a crypto hack and that led to their shut down e.g. Conrail and MT Gox
Furthermore, individual traders who have fallen victim to a wallet hack can:
- Change their login details and enable two-factor authentication to log out the hacker.
- Notify their exchange/provider since they may be able to retain some useful information about the transaction
- Check their devices for malware and fix them.
- Use a cold wallet instead of a hot wallet
- Spread their investments across exchanges to curb future losses.
Pro tip: You can visit sites like “Get Safe Online” and “Cyber Aware” to see how to improve your general online security.
[Suggested Read: How To Spot A Fake Crypto Exchange – 7 Red Bell Alerts]
Learn Crypto Trading!
To help you trade crypto profitably and curb your risks, we curated the perfect course for you.
Go to www.ctmastery.com to enroll in our Cryptocurrency Trading course and thank me later.
You can also join our Telegram community at https://t.me/ctmastery.
5. Conclusion
Although cryptocurrency gives us absolute control of our finances, our funds are only as safe as the security measures crypto platforms have in place.
Crypto hack can happen to any wallet, exchange, or blockchain so long as a thief sees an opportunity there.
While affected traders may be reimbursed in some way, crypto hack can have a negative effect on the value of tokens and even the whole market.
Therefore, both users and crypto service providers must take adequate measures to prevent a crypto hack from happening.
We have now come to the end of this article, I hope it was worth your time.
Tell me in the comments if you have ever been a victim of a crypto hack and how you recovered from it.
Also, share this post with your friends, thank you!



0 Comments